Thoughts
This was a fairly easy stegno challenge, only if one properly understood the
major hint. Use of CyberChef gives an extra advantage in automating and saving
time.
Brief
- Figure out encryption type.
- Brute force all keys
- Use the keys to build up the flag.
Hints
The challenge name eaxy seems a bit peculiar, s is replaced by x, which
gives off a major clue. The x could be multiplication, which could be a
starting point, but while thinking in a more cryptographical sense, the most
viable takeaway from this x is XOR.
CyberChef
From the challenge name, we deduced that the file is XOR crypted.
We use CyberChef “XOR Brute Force” method and import the file directly.
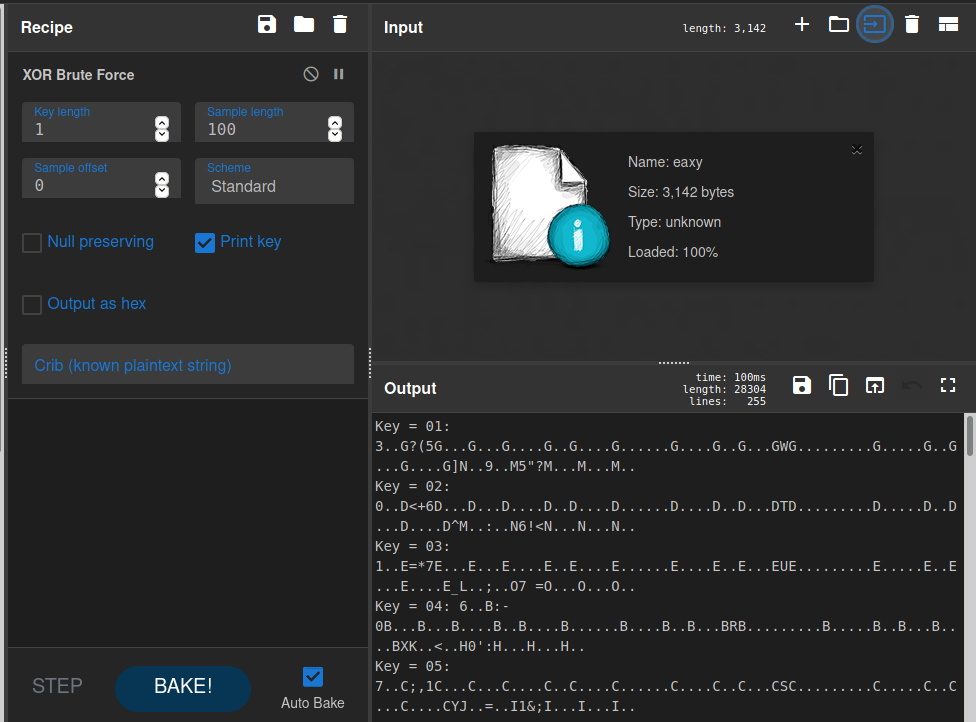
Here we notice some garbled text in the output. We then use the “known
plaintext string” to filter out the results.
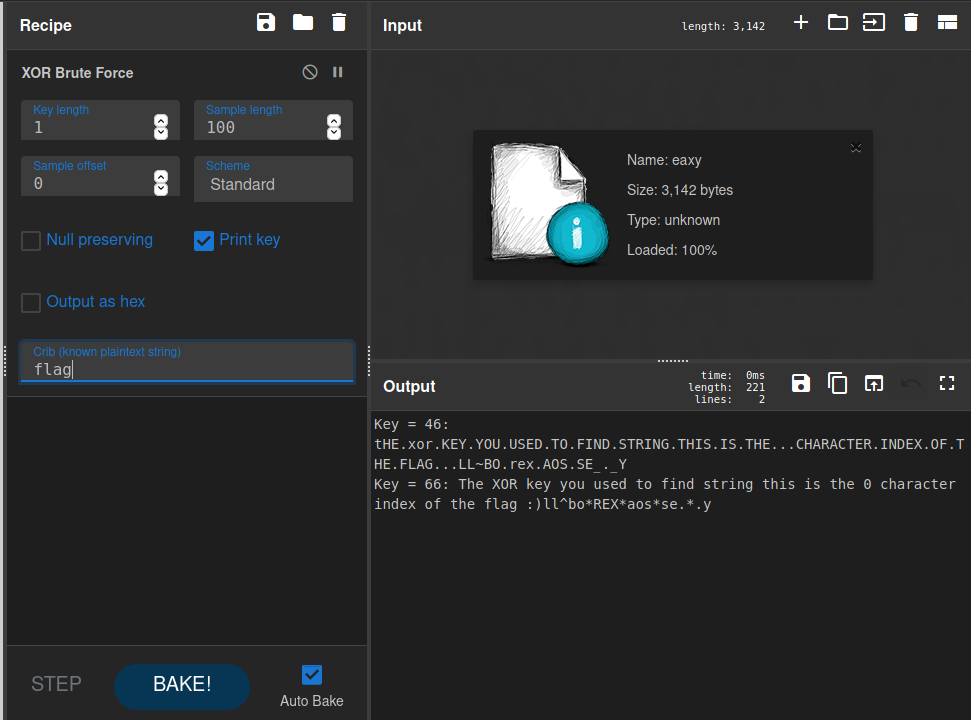
We notice the following:
Key = 66: The XOR key you used to find string this is the 0 character index
of the flag :)
From the above output, it is evident that we have to brute force all the keys and get the flag by placing the keys in specific order that is specified as
the index.
We change the Sample length to -1 to enable scanning of the entire file.
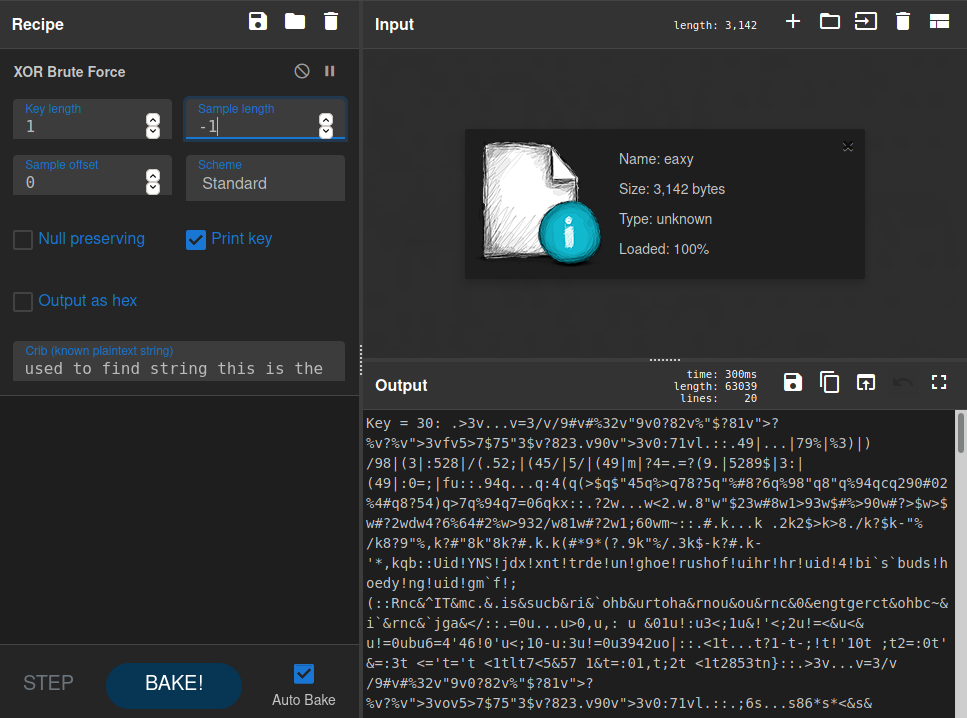
We now have the keys and the orders in which it will be placed, but we have to cleanup the unwanted data, for that we copy the data to our local machine and use some linux-fu.
Building up the flag
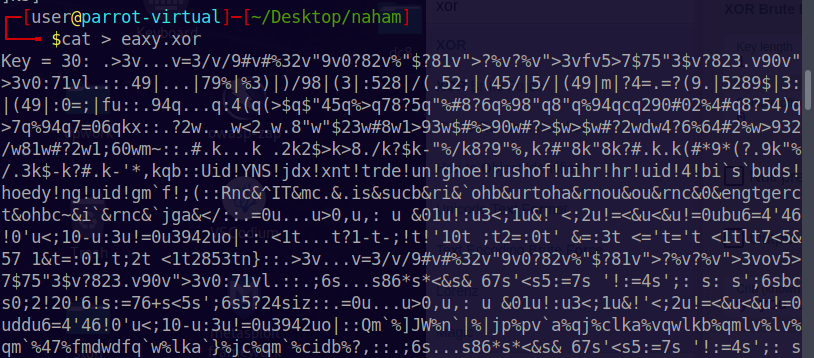
I used awk to quickly filter out the data, and to give me only the key and
position of the flag.
1 | awk '/Key = /{print $3}; {for(i=1;i<=NF;i++) if($i=="this" && $(i+1)=="is") print $(i+3)}' eaxy.xor |
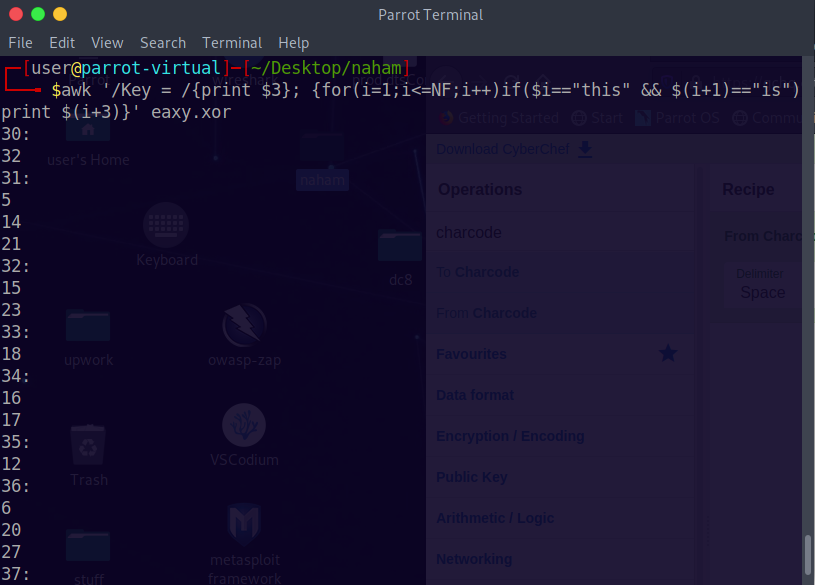
We get the following output:
1 | 30: |
The numbers ending with a semicolon “:” is the key, followed by the positions
of the flag directly below it.
Now we could make a simple python script to directly sort the positions with
the keys to get the flag, but I found it convenient to do it manually (with
pen and paper). After sorting the positions with the key values, we get the
following:
1 | 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 |
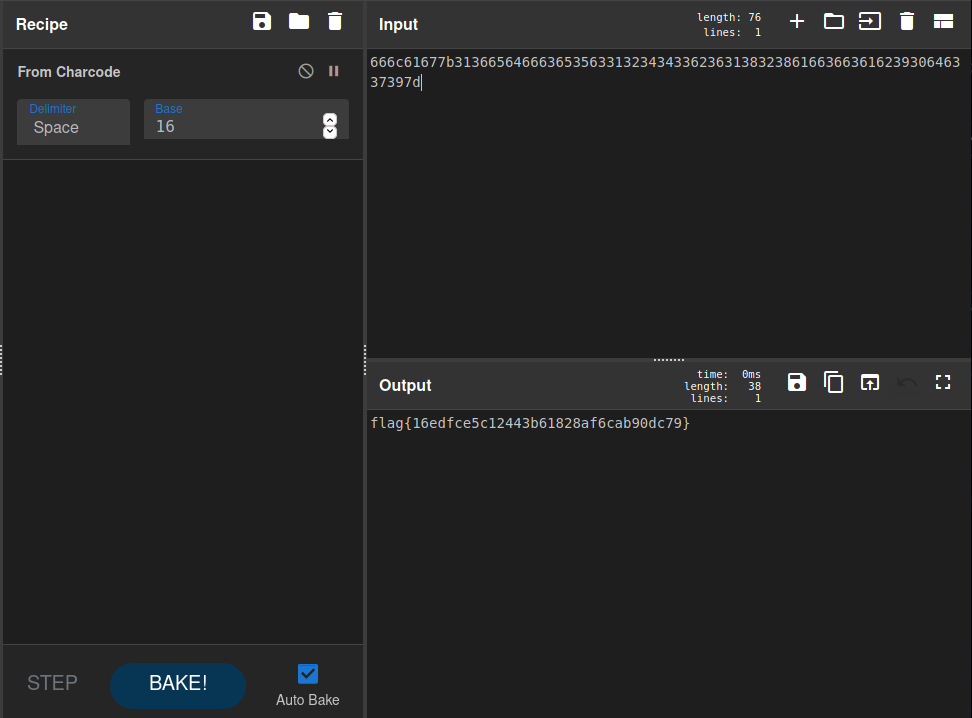
Where the final flag is in ASCII; using CyberChef one last time, we decode
these ASCII values to their corresponding characters to get the flag.
About this Post
This post is written by Gliston, licensed under CC BY-NC 4.0.