Thoughts
This was rated as an ‘easy’ challenge, but I really had a hard time solving it. Thanks to all the people on discord giving hints, without which, I would not have been able to solve this challenge.
Brief
- Enumerate to find publicly accessible .git folder
- Clone the .git folder to local machine
- Explore .git objects to get the flag.
Hints
Let’s start off by looking at the hints for this challenge. (Note: this challenge unlocks only after completing other challenges, so the hints were spread across discord, the CTF website and the previous challenges as well.)
Hint 1:
From the previous challenge:
“Vela, can we please stop sharing our version control software out on the public internet?”
Hint 2:
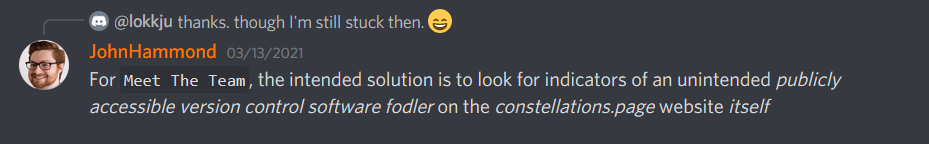
Hint 3:
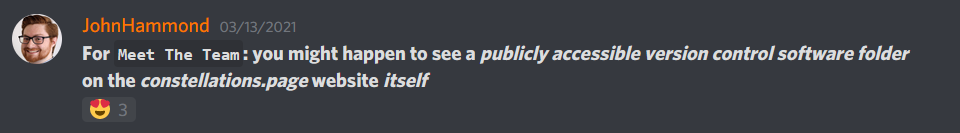
Recon
From the hints it is obvious that the flag is in a publicly hosted version control software (.git specifically). Googling a bit on publicly available .git folders, I found out this site:
When deploying a web application, some administrators simply clone the repository. Most version control systems create a meta/tracking folder in the root directory of the project. For example:
- git creates a .git/ folder containing a full copy of the repository.
- Others may follow a similar approach (e.g. SVN).
To clone the .git repo from the website, we use GitTools (which is also mentioned in the above site). We have to clone the entire git repo to our local machine to do some further enumeration; for this we use the Dumper tool in GitTools.
Exploring .git
Taking a look at the cloned .git repo on our machine, we notice the following files:
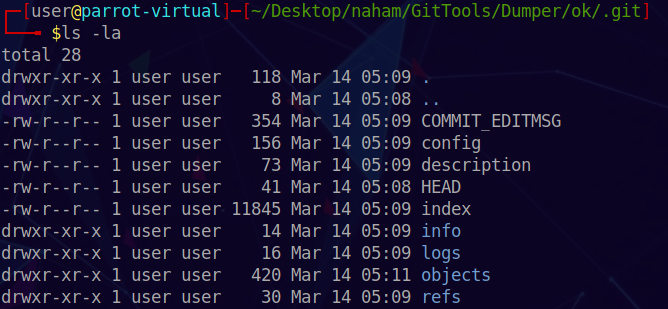
We take a note of the following:
There are 3 kinds of objects in the .git repo:
- Blob – The actual data (e.g. source code)
- Tree – Grouping blobs together
- Commit – A specific state of a tree with more meta information (e.g. author/date/message)
All these together are used by git to maintain the repository. The files either refer to an object by its hash or another file referencing an object and so on.
Let’s now take a look at what the master is pointing to:
1 | cat .git/refs/heads/master |
The output is a SHA1-hash of the object.
We can now find out what kind of an object this hash is pointing to:
1 | git cat-file -t <hash> |
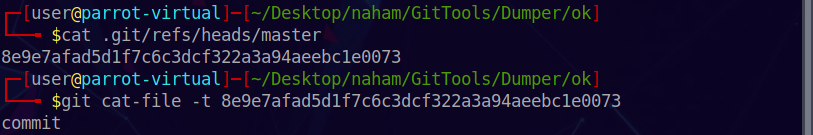
The reference master points to a commit with the hash 8e9e7afad5d1f7c6c3dcf322a3a94aeebc1e0073.
Now let’s try to see the git log to find out any information:
1 | git log --pretty=oneline |
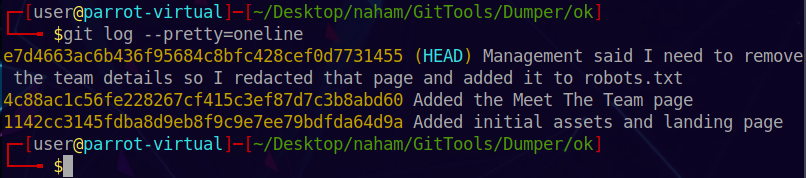
From the commit messages, we notice that the current HEAD is the state of the repo where the page is deleted. We somehow need to access the page using the git repo. Also we find out that the page is redacted in robots.txt. Looking at robots.txt we find that the filename is “meet-the-team.html”.
Getting the flag
Now let’s get details about the commit with hash 4c88ac1c56fe228267cf415c3ef87d7c3b8abd60, this is the hash when the “meet-the-team.html” page is added:
1 | git cat-file -p 4c88ac1c56fe228267cf415c3ef87d7c3b8abd60 |
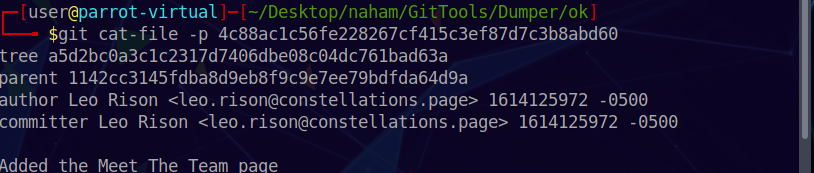
We have the file hash, we just need to display its contents with:
1 | git show 4c88ac1c56fe228267cf415c3ef87d7c3b8abd60 |
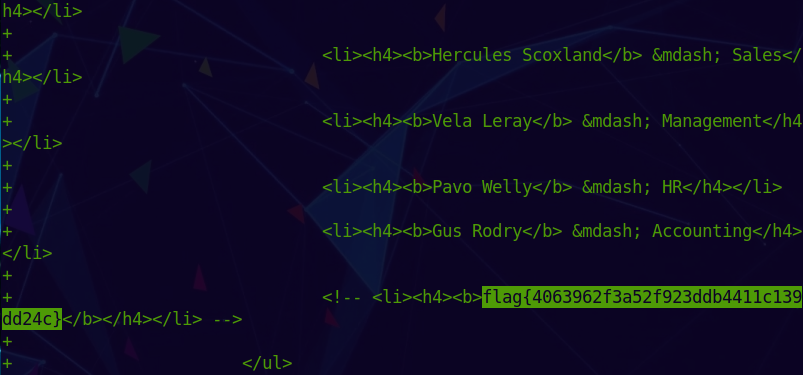
And we get the flag. p.s.: we also get the names of the team members that is required for the next challenges.
About this Post
This post is written by Gliston, licensed under CC BY-NC 4.0.